Master cyber attacks with Corelight
Corelight's "open" Network Detection Response (NDR) platform is powered by the open source community and relies on technologies such as Zeek et Suricata . Corelight protects some of the world's most critical businesses and government agencies.

Evidence-Based Security: Why?
Cyber defense elites recognize that alerts can, and will, go unnoticed. They know that a defense strategy based primarily on the evidence is their best opportunity to pick off the most advanced opponents in the act.
Evidence helps elites increase visibility, access powerful analytics, accelerate investigations, and optimize threat hunting.
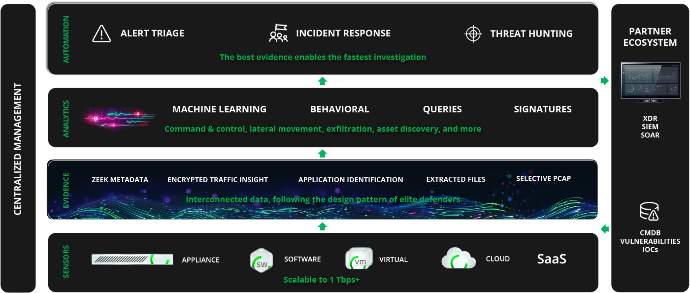
A state-of-the-art platform.
Monitor your network traffic on premises or in the cloud with physical or virtual capture probes, the choice is yours.
Combine network analysis tools, intrusion detection system or if necessary de packet capture, with artificial intelligence in the form of "machine learning", analytical data powered by powerful telemetry, "SOAR" scenarios, and you will boost your abilities to make better decisions to increase the effectiveness of your responses.
Complete visibility
Get an impressive view of your organization, items connected to your network, access to details such as SSH inferences, DNS query/responses, file hashes, TLS connections, HTTP content.
Corelight generates the telemetry needed to provide all the contextual details Security Operation Centers (SOCs) need to unmask hidden attacks and reduce an adversary's dwell time.
Expert Hunting
Specific, rich and organized security evidence allows you to uncover vulnerabilities, attacker artifacts, critical misconfigurations, indicators of compromise, or even undetected attacks.
Corelight helps you mitigate your cyber risks.
The best defense relies on evidence.
With Corelight, be in the best position to manage your risk when an alert occurs, when a major attack is detected, or when you remediate a security breach.
How to detect the top 5 Advanced Persistent Threats (APT)?